
The best system is the one that effectively manages the network resources at the same time giving the users the top services. To achieve this, it is necessary to have excellent understanding of the set requirements so as to know how to plan and execute a system that performs optimally. As the network’s complexity constantly increases, the task of managing it becomes difficult. This has triggered increased research on how to effectively manage the network resources and users. There are two common techniques applied in the management of the network resources: work or domain based.
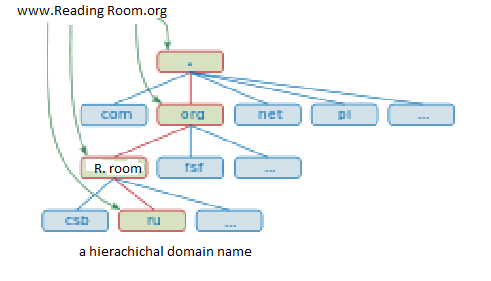
In a domain based system, there exists a single centralized network administration point. This point is used to grant network access permissions to network resources that are maintained on one server. This type of server is known as the domain controller. In this type of system, a hierarchical arrangement is used in assigning users, who collaborate with other organizations departments, permission to access the network resources (Evans, 12-15). This type of system offers higher versatility, flexibility and security than the work based system; however, its more complex. The old network at Reading Room cannot guarantee security and data reliability. To achieve quality, organized and more secure data at Reading Room, various measures under a domain based system have to be implemented. They include account naming convention, password change policy and rights of specific users that can be implemented by the administrator.
The account naming convention requires all the users to be identified using unique name. To achieve this, user’s unique ID or special suffixes can be used. Each one with a unique ID can only access information using a password adhered to set policies. Password policy entails rules governing its usage to raise computer or system security. In a domain based system, only the administrator can change passwords. This policy requires the them to be changed after a certain period and must meet certain complexity specifications. Using rights of specific users means that only a certain group is privileged to access certain information (Van & Annemiek, 176-180). The new design will give the user rights to accounts or finance departments to access the shared dedicated drives. Additionally, in the new design, each computer and department should be uniquely identified. It helps the network administrator easily identify and know any users who access certain network resources. The password can be used to limit access of certain information on the servers. Each department should employ password to their shared drive so that only members of that department can access the information.
Task 2
Hardware and software requirements are highly dependent on the role of the user. Users in the administration departments are less required to handle computational and processing activities, therefore, they may require hardware with low profiles. On the other hand, departments comprising designers and back end developers are highly involved in computational and processing activities. Thus, they require hardware with high memory and graphics capacity and processing power. The open system interconnection model is seven layered and provides a reference for complex network aspects. The seven layers divide the various services and functions provided by the software and the hardware in a network.
The upper layer of the model consists of the application, presentation and session layers which are implemented in software. Network and transport layers are implemented in software and are mostly responsible for protocols used in delivery and routing of packets in the network (Harwood, 31). The data link layer is implemented in both software and hardware. WAN and LAN specifications are defined in data link and physical layers.
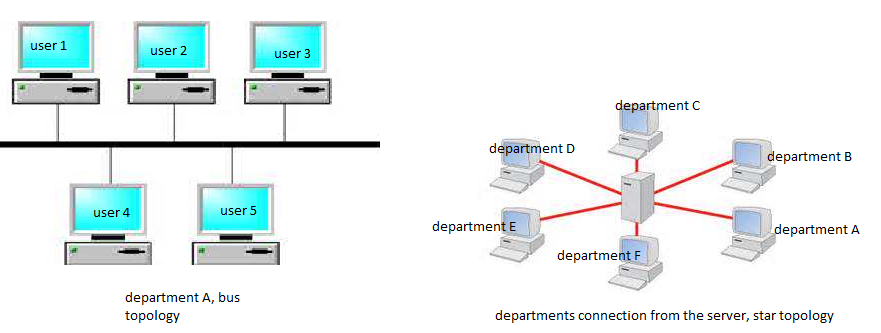
The star topology would be the best topology for the computer arrangements in this case. Each network host is connected through a central connection; it gives the administrator the right to ensure data security and integrity by controlling those who access the data. From the administrator, each of the devices in the Reading Room can be connected using star topology. A bus topology can be used to connect the users at department level.
Reading Room intends to isolate the critical departments from the access of everyone apart from the intended departments. This can be achieved through IP addressing, selecting routing protocols based on the design topology and server access layer design. First, the future growth should be taken into consideration while building server farms, IP address allocation and dynamic routing.
Since this is a LAN network a dynamic host configuration protocol is the best protocol to dynamically assign host IP address from the centralized server (Watson, 37-40). This helps in reducing the overhead of administrating IP addresses. Only the client devices connected to the network are assigned IP addresses thus consume limited IP address space. The network operating system is a computer networking oriented software that can be run on the server to facilitate it in managing resources and users. Client server and peer to peer are the two major types of network operating system. To implement the network at the Reading Room ltd, the client server model is preferred. It allows centralization of functions and applications in a one dedicated server, thus raising security of the network.
The network also needs a client operating system. This helps the client to effectively interact with the network. Windows versions are the most recommended ones. For the purposes of troubleshooting, the windows have the network diagnostics framework. Windows 7 contains an inbuilt new netsh.exe context and netsh trace for network tracing. The netsh trace allows selective tracing for providers and scenarios.
Task 3
This task ensures security of the network resources using windows server based features such as the distributed file system, file /folder security, compression and encryption mechanisms, implementing security certificates and web access of the documents. The design to be implemented at the Reading Room Ltd should be able to manage server resources efficiently, availing them to users and at the same time ensuring security. Due to the high number of departments the administrator may find it hard to keep the users and the files connected. Additionally, distributing servers results in making files available to more users and increases the costs involved.
Distributed file system assists the administrator in increasing file access performance, efficient sharing of files among geographically separated departments and enables backup of the files (Kistler, 113-117). Windows Server 2003 operating system offers this feature using DFs namespace and DFs replication technologies. This is the operating software to be employed in Reading Room Ltd servers. In addition, the system employs file security techniques. File encryption entails encoding the file message with a key that is only known to the sender and receiver of the message. This gives the file security during transmission.
File compression is used to archive the files and folders, thus reducing the transmission time and saving the disk space. There is also folder/file certificate, which is a security measure implemented at the message layer (Noergaard, 59-60). It ensures a secure exchange of message between two parties, X.509 is an example of file certificate (Reisman & Mitch, 89-93). To ensure security, the Reading Room intends to distribute trusted root certificates to enable its employees to use the PKI system.
Web access to the documents is intended to allow employees to remotely access office documents. This aspect is controlled by the security rights assigned to the employees. The new Reading Room Ltd network will comprise the above security measures to ensure reliability and integrity of the company’s data (Xu, 234-237). Some are independent porgrams while others are inbuilt in the windows server operating system.
Task 4
To configure the server so as to host the company’s website and allow staff groups to manage their own websites, information service manager is needed. It enables controlling of the hosted websites on the server. This is an administrative tool which needs to be configured after installing Windows operating system in the Windows control panel. To configure it, one needs select control panel at the start button, then select turn windows features on or off. Afterwards, they need to click the internet information services, followed by world wide web services to install additional development tools used in website creation. On clicking the OK button, Windows automatically installs and configures the internet information services on the machine (Shinder, 70-72).
Network Address Translation (NAT) is a method of substituting the packets’ real address with a public address that can be used on a public network. This way the private IP networks are able to connect to the internet. It acts as a security measure since it hides the internal IP addresses thus discouraging direct attacks. In addition, it allows the administrators to control the access restrictions since they can change IP addressing schemes without interfering with the externally available public addresses.
Configuration is done by choosing the interface connecting to the internet at the drop-down menu, then selectiong the networks to share the WAN interface in the NAT configuration set (Muelle & Russ, 45-49). Configuring the NAT depends on whether it is being configured as static or dynamic. Statically configured NAT appropriate mapping entries in the NAT table are created. In dynamically configured NAT, a pool of addresses used for translating is created and an access list to identify the address to be translated is also created.
Works Cited
Evans, Eric. Domain-driven Design: Tackling Complexity in the Heart of Software. Boston [u.a., 2004. Print.
Harwood, Mike, and Drew Bird. Network+ Training Guide. Indianapolis, Ind: Que, 2002. Print.
Kistler, James J. Disconnected Operation in a Distributed File System. Berlin, Heidelberg: Springer Berlin Heidelberg, 1995. Internet resource.
Mueller, John, and Russ Mullen. Mastering Iis 7 Implementation and Administration. Norwood Mass: Books24x7.com, 2007. Internet resource.
Noergaard, Tammy. Embedded Systems Architecture: A Comprehensive Guide for Engineers and Programmers. Amsterdam: Elsevier/Newnes, 2005. Internet resource.
Reisman, Brian, and Mitch Ruebush. Mcse: Windows® Server 2003 Network Security Design Study Guide. Hoboken: John Wiley & Sons, 2006. Internet resource.
Shinder, Thomas W. D. S. D. L. Mcse Planning and Maintaining a Windows Server 2003 Infrastructure: Exam 70-293 Study Guide … Guide & Dvd Training System. S.l.: Syngress Media Inc, 2003. Internet resource
Van, Bon J, and Annemiek . Veen. Release & Control for It Service Management: Based on Itil : a Practitioner Guide : Configuration Management, Release Management & Change Management. Zaltbommel, Netherlands: Van Haren Pub, 2007. Print.
Watson, Ruth A. Introduction to Operating Systems and Networks. Upper Saddle River, N.J: Pearson Prentice Hall, 2004. Print.
Xu, Zhuo. Designing and Implementing Ip/mpls-Based Ethernet Layer 2 Vpn Services: An Advanced Guide for Vpls and Vll. Hoboken, N.J: Wiley, 2013. Internet resource.
|
Grammar
D
|
Formatting
D
|
Organization
B
|
Style
C
|
